 Inbound Links – Still Important for Google
Inbound Links – Still Important for Google
As I have written many times (8/15, 7/18, 8/17, 2/17, 7/15, etc. ) Google still considers Inbound Links (links that come from other websites) as an important ranking factor. The more links you have FROM a related / trusted source, the higher your site will rank. Links on other web sites are like votes of trust, credibility, and authority. The more quality links your page has, the more votes, the better your ranking.
Links from fly-fishing blogs, sewing journals, backyard grilling sources are nice, but these will NOT help your rankings!
 Outbound Links (links from your site to other sites) are OK, don’t have too many of these. Outbound links should just be used in a way that appears natural to the user.
Outbound Links (links from your site to other sites) are OK, don’t have too many of these. Outbound links should just be used in a way that appears natural to the user.
Reciprocal Links (trading links with other sites) are OK, as long as these appear natural.
How to obtain inbound links? Go to your business related web sites, sources for related information, Chamber of Commerce, business associations and see if they list other companies. If they do, look for a ‘Add a Business Listing’ link or simply ask their webmaster.
How can you determine how may links you have? Go to https://lxrmarketplace.com/seo-inbound-link-checker-tool.html and enter your domain.
Would you like to know how many inbound links your competition has? Use this same link. More than your competitors?
|
|
|
 Safe Email Practices – Have a Healthy Suspicion
Safe Email Practices – Have a Healthy Suspicion
- Protect yourself from spam, phishing and malware – Viruses are often spread through e-mail. You can greatly reduce the spread of e-mail viruses by using antivirus software, using only e-mail services that offer automatic antivirus protection (such as GMail, YahooMail, Oultlook.com, etc.), opening e-mail only from trusted sources, opening only attachments you’re expecting, and scanning attached files with antivirus software before opening them.
2. Email Sources – Anyone can create an account and have it appear to come from ANY address. Would you open up an email from Mickey@Disney.com? BillG@Microsoft.com? rich@richswebdesign.com? (see ‘Harponing’ below)
3. Spam is loosely defined as unsolicited bulk e-mail and loosely correlates to the junk mail that turns up in your home mailbox. Proper emails should have a ‘Unsubscribe’ link near the bottom of each email. This is recommended, but you can always right-click the email, select ‘Junk’ / ‘Block Sender’. Don’t open unsolicited e-mail. If you accidentally open spam, don’t click any links!
4. Phishing scams are designed to steal consumers’ personal information. They often use doctored and fraudulent e-mail messages to trick recipients into divulging private information, such as credit card numbers, account usernames, passwords, and even social security numbers.

5. Harpooning / Whaling – A type of scam in which phishers find the name and email address of a company’s top executive or team of executives (information often freely available on the web), and craft an email specific to those people and their role at the company. The email attempts to lure the executives into clicking on a link that will take them to a website where malware is downloaded onto their machines to copy keystrokes or ferret out sensitive information or corporate secrets
Online banking and e-commerce are generally safe, but you should always be careful about divulging personal and corporate information over the Internet. Phishing messages often boast real logos and appear to have come from the actual organization, but those messages are frequently nothing more than copyright infringements and faked addresses.
6. Grammar – Look for proper grammer, sentence structure, mispelings and not perfectly formated emails from banks, Apple, credit card companys, etc. (… Did you catch these four?) Legit companies know how to spell.
7. Updating your login info / Confirm your account – These are big red flags and should be seen as highly suspicious. ‘Account locked’, ‘Password reset’, any emails from the IRS are all red flags. Legit companies don’t request your sensitive information via email. Legit companies usually call you by your name.
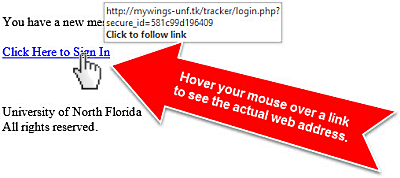
8. MouseOver Links – Holding your mouse over links (do not click) will tell you a lot about the authenticity of a given email! Which addresses seem legit? … login.USBank.ch?, private.apple.us? , no-reply.BankofAmerica.com.ru?
9. Email Attachments – Consider the source and whether you are expecting an attachment. You should check the file type of any attachment before opening it. Malware and viruses can be hidden in files of the following file extensions; .ade, .adp, .asf, .bas, .bat, .chm, .cmd, .com, .cpl, .crt, .exe, .hlp, .hta, inf, .ins, .isp, .js, .jse, .lnk, .mdb, .mde, .mov, .msc, .msi, .msp, .mst, .pcd, .pif, .reg, .scr, .sct, .shs, .swf, .url, .vb, .vbe, .vbs, .wsc, .wsf, .wsh,
Even Microsoft Office documents (.docx, .xlsx, and .pptx) and PDFs can contain malicious links and macros that can download malware onto your mobile or computer.
The following image, sound and video formats should be safe though: .gif, .jpg, .tif, .tiff, .mpg, .mpeg, .mp3, and .wav. If you’re unsure, it’s good practice to email the sender to confirm they meant to send the attachment.
In summary, be wary of free money and urgent requests. Cross-check unexpected emails from people in authority over the phone or in person before sharing or downloading information. Many phishing emails only need one click to give the hacker access to your otherwise secure systems.
Stay smart about security. Take precautionary steps now to prevent attacks later!
P.S. – ‘Reply-All’ – This is nothing to do with phishing or viruses, but PLEASE be considerate about using ‘Reply All’.
|
|
|


