Latest WordPress Security News – Below)
 WordPress web sites are becoming more and more time consuming on a weekly / daily basis to keep up with the following items:
WordPress web sites are becoming more and more time consuming on a weekly / daily basis to keep up with the following items:
1. WordPress Plugin Updates (Careful use of any plugin, theme and WordPress Core updates)
2. Regular Scheduled Backups (Weekly / Monthly)
3. Proactive Security Updates ( WP Security Scan)
4. Performance Optimization ( reCAPTCHA installation on forms, image optimization)
5. Malware prevention / cleanup & Performance Scans ( WordFence & GravityScan)
6. 24/7 Uptime Monitoring
7. Google’s Site Kit – Google’s latest one-stop tool to deploy, manage, and get insights from critical Google tools.
WordPress websites need continuous monitoring, maintenance and upgrading so that it can give optimum performance and stay safe from hackers. But if your website is hacked, someone should be there to restore the site from clean/latest backup.
Websites aren’t paintings that you hang up on the wall after they’re complete; they are an investment that needs to be looked after to keep the positive ROI.
With WordPress maintenance, I am pledging time to be your client’s website “bodyguard.” If anybody messes with your business, I’m going in there, guns blazing. Otherwise, you’ll sit quietly in the corner, keeping one eye shut and the other on the door.
Yes, this is different than regular ‘site maintenance‘, which has been outlined in your contracts. ‘Site maintenance’ has been focused on making changes to content / images on your current pages. Changes prices, changing content, adding fresh news are all examples of your existing ‘site maintenance’ agreement. WordPress Maintenance deals with security, backups, prevention and keeping up with various plugin updates.
Security is one of the most important aspects of running a website these days, as there truly are a lot of malicious people out there that can and will try to target your website (whether to try and steal your data, use your PC for a DDoS, or a number of other reasons known only to them).
WordPress web sites are constantly being hacked, or rather are ATTEMPTED to be hacked on a daily basis. WordPress security is all about proactivity. You know what they say, an ounce of prevention is worth a pound of cure, especially on the web. Most WP attacks initiate from Russia, China, France, India, Ukraine and the good ol’ USA.
(Great WP Security Article) – WordPress Security: The Ultimate Guide
(Best WP Security Plugins) – WordFence, iThemes Security, Sucuri Security, All in One WPSecurity, BulletProof Security. (Article)

Latest WordPress Security News
July 2021
Update these plugins immediately -> VDZ Verification, VDZ Callback, Wonder PDF Embed, Wonder Video Embed, Profile Builder, VikRentCar Car Rental & YouTube Embed.
Uninstall these plugins immediately -> My Site Audit, Social Tape, Telugu Bible Verse Daily, and others.
Update these themes immediately -> Newspaper
May 2021
For the last few days, I have been upgrading all of RWD’s ‘Proactive WordPress Security, Backups, Malware Prevention’ clients with various tools / plugins to prepare for ‘Google’s Page Experience‘ update coming in the next month or two.
The two primary area I am tackling first are:
1. Optimizing Images – The WordPress plugins that I prefer are – ‘Smush‘, ‘Optimole‘ or ‘Image Optimizer WD‘. Each of these tools take each web site image and reduces the file size so that it loads faster, while maintaining the image quality. Since loading time is one of the important aspects of what Google will be measuring, this is important for your site.

2. Web Site Cache – ‘Cache’ refers to memory and how your computer remembers images, pages and scripts when loading each page in your browser. If it weren’t for ‘cache memory’, every time you visited various pages on any web site, each page would have to load the logo / header / menu / structure each and every time. This would take FOREVER!

My best tool is ‘W3-Total Cache‘ – W3 Total Cache (W3TC) improves the SEO and user experience of your site by increasing website performance and reducing load times by leveraging features like content delivery network (CDN) integration and the latest best practices. Page load times, web server performance, and bandwidth are all improved with W3 Total Cache.
Only 2-3 client sites have NOT accepted these above WordPress improvements. After the installs, these sites did not show images properly or much slower. In these cases, I removed / uninstalled the plugins and used other WordPress tools as alternatives.
In the next week or so, I will logging into each client Google Search Console account to see if there are any errors showing. If so, I will fix these.
If you remember the items that Google will ne looking for in this ‘Page Experience‘ update, they are … mobile-friendliness, safe-browsing / HTTPS, alt tags, poor use of intrusive pop-ups, etc.
July 2020
WordPress Plugin Vulnerabilities
Wise Chat – Powie’s WHOIS Domain Check – Knight Lab Timeline – Page Builder: KingComposer – SendPress Newsletters – All in One SEO Pack – All of the above plugins have been updated and verified.
Nov 2019
A few new WordPress plugin and theme vulnerabilities were disclosed during the second half of November, so we want to keep you aware. Several new WordPress plugin vulnerabilities have been discovered this November. Make sure to follow the suggested action below to update the plugin or completely uninstall it.
Sassy Social Share – version 3.3.3 and below is vulnerable to a Cross-Site Scripting attack.
WP Maintenance – version 5.0.5 and below is vulnerable to a Cross-Site Request Forgery to Stored Cross-Site Scripting attack.
Jetpack versions 5.1-7.9 have a vulnerability in the Shortcode Embed Code.
Safe SVG version 1.9.5 and below is vulnerable to a Cross-Site Scripting Bypass attack.
Tidio Live Chat version 4.1 and below is vulnerable to a Cross-Site Request Forgery leading to a Cross-Site Scripting attack.
Blog2Social: Social Media Auto Post & Schedule version 5.8.1 has a Cross-Site Scripting vulnerability.
WP Google Review Slider version 6.1 is vulnerable to an Authenticated SQL Injection attack.
Zoner Real Estate Theme version 4.1.1 and below a Persistent Cross-Site Scripting and Insecure Direct Object Reference vulnerabilities
How to Be Proactive About WordPress Theme & Plugin Vulnerabilities
Running outdated software is the number one reason WordPress sites are hacked. It is crucial to the security of your WordPress site that you have an update routine. You should be logging into your sites at least once a week to perform updates.
Automatic updates are a great choice for WordPress websites that don’t change very often. Lack of attention often leaves these sites neglected and vulnerable to attacks. Even with recommended security settings, running vulnerable software on your site can give an attacker an entry point into your site.
iThemes Sync is our central dashboard to help you manage multiple WordPress sites. From the Sync dashboard, you can view available updates for all your sites and then update plugins, themes and WordPress core with one click. You can also get daily email notifications when a new version update is available.
Breaches From Around the Web
We include breaches from around the web because it is essential to also be aware of vulnerabilities outside of the WordPress ecosystem. Exploits to server software can expose sensitive data. Database breaches can expose the credentials for the users on your site, opening the door for attackers to access your site.
T-Mobile is the latest company to fall victim to a data breach.
Sept 2019
Best WordPress Security Plugins in 2019
1. Wordfence Security
Active on over three million WordPress sites, Wordfence Security is definitely one of the most popular and well-known WordPress security plugins.
It does a great job of protecting your site in a variety of ways, including:
-
- Web application firewall to block malicious traffic before it can do anything to your site.
- Security scanner to check for malware and other malicious exploits.
- Login page hardening with two-factor authentication and/or a login page CAPTCHA.
- Lots of various security hardening rules.
Wordfence also gives you a really nice dashboard to view important aspects of your site’s security:
2. iThemes Security
iThemes Security is the flagship security plugin from iThemes, which was acquired by Liquid Web back in early 2018.
Like Wordfence, it comes in both a free and a premium version (the free version was previously named Better WP Security).
iThemes Security gives you 30+ tools to harden your WordPress site’s security. In the free version, that’s tools like:
-
- Brute force protection
- File permission monitoring
- File change detection
- IP bans
- Etc.
Everything is modular, which means you can easily activate or deactivate features as needed:
3. All In One WP Security & Firewall
All In One WP Security & Firewall is a 100% free WordPress security plugin, which makes it a great option for those on a budget.
It helps you implement a ton of different security hardening principles, along with a neat scoring system to help you figure out what’s important:
4. Sucuri Security
There are two parts to the popular Sucuri Security plugin at WordPress.org:
-
- The free plugin, which implements some basic hardening and file integrity checks.
- The paid Sucuri firewall service, which you can implement via the plugin.
In total, the plugin can help you:
-
- Monitor file integrity.
- Scan for malware on the front-end of your site using the public security scanner (this would not catch files just sitting on your server).
- Check for blacklisting in Google and other places.
- Track user logins.
- Implement various hardening tips, like blocking PHP files in wp-content.
- Send email alerts for important issues.
Others – https://wplift.com/best-wordpress-security-plugins
Other WPLift Articles on Security –
July 2019
New WordPress plugin and theme vulnerabilities were disclosed during the last half of June. All of these have updates / patches that should be installed, except the Real Estate Manager (in red)
- The Messenger Customer Chat plugin, version 1.2 and below, is vulnerable to a Cross-Site Request Forgery attack. The vulnerability will allow an attacker to change some of the WordPress site settings.
- The Support Board – Chat And Help Desk | Support & Chat plugin, version 1.2.8 and below, is vulnerable to a Cross-Site Scripting attack.
- The Seo by Rank Math plugin, version 1.0.26 and below, is vulnerable to a Cross-Site Scripting attack.
- The WP-Members Membership plugin, version 3.2.7 and below, is vulnerable to a Cross-Site Request Forgery attack. The vulnerability will allow an attacker to create, edit, and delete new fields.
- The Real Estate Manager plugin is vulnerable to a Plugin Arbitrary Settings Update attack. The lack of authorization and CSRF checks in the
save_admin_settings()AJAX function is the cause of the vulnerability. – This plugin does NOT have a patch and should be removed! - The LionScripts: IP Blocker Lite plugin, version 10.3 and below, is vulnerable to a Cross-Site Request Forgery attack that could lead to an Arbitrary File Upload attacks.
- The WebP Express plugin, versions 0.14.10 and below, are vulnerable to a multitude of attacks, Cross-Site Request Forgery, Arbitrary File Upload, Cross-Site Scripting, an Unauthorized Access attacks.
- The Import users from CSV with meta plugin, version 1.14.1.2 and below, is vulnerable to a Cross-Site Scripting attack.
- The Facebook for WooCommerce plugin, version 1.9.12 and below, is vulnerable to a Cross-Site Request Forgery attack.
- The CP Contact Form with PayPal plugin, version 1.3.01 and below, is vulnerable to a Cross-Site Scripting attack.
- The Share This Image plugin, version 1.19 and below, is vulnerable to a Cross-Site Scripting attack.
- The ads-for-wp plugin is vulnerable to a Cross-Site Request Forgery attack.
- The ACF: Better Search plugin, version 3.3.0 and below, is vulnerable to a Cross-Site Request Forgeryattack.
June 2019
Using a professional / reputable hosting company for your WordPress hosting is an important aspect of your overall site security. The company I use for 65% of my clients is Buzix and they are very good in security. The other hosting companies that RWD uses come from site that have been hosted at another hosting company. When upgrading a WordPress site, if the client so chooses, we will not move the hosting.
 Service Vulnerability: Four Popular Hosting Companies Fix NFS Permissions and Information Disclosure Problems –
Service Vulnerability: Four Popular Hosting Companies Fix NFS Permissions and Information Disclosure Problems –
Last year, Wordfence published two disclosures of service vulnerabilities on hosting platforms. The first one included a trio of brands: Hostway, Momentous, and Paragon Group. The second was for MelbourneIT. In all cases, Wordfence was happy to report that the affected companies took our disclosures seriously and moved quickly to fix the problems.
Today Wordfence is announcing a similar disclosure for several brands owned by Endurance International Group, including iPage, FatCow, PowWeb, and NetFirms. A pair of vulnerabilities on these platforms allowed attackers to tamper with customers’ databases directly, without actually accessing their websites.
May 2019
![]() New report finds attacks on consumers down 24 percent, attacks on businesses up 235 percent. Cybercriminals went after businesses in a big way. Can consumers breathe a sigh of relief? Considering the businesses have your data, probably not…
New report finds attacks on consumers down 24 percent, attacks on businesses up 235 percent. Cybercriminals went after businesses in a big way. Can consumers breathe a sigh of relief? Considering the businesses have your data, probably not…
What is a SQL injection attack? Criminals use SQL injections to exploit software vulnerabilities and gain access to your data…
(More info at https://blog.malwarebytes.com
Feb 2019
What Attackers Were Up To
For the week there were a total of 223 attacks blocked. I was excited to see that all of them were blocked by the Wordfence real-time IP blacklist. We are used to seeing really high percentages blocked by our blacklist – usually in the high 90s. The real-time IP blacklist is a Premium feature that blocks all requests from IPs that are actively attacking WordPress sites.
Attacks originated from 14 unique IP addresses from around the world. Of the countries represented, Germany was the origin for the most attacks at 85. India was second with 61 and France was third with 45. Other countries represented were Ukraine, South Africa, China, Italy and the United Kingdom.
Next we’ll break down what they were trying to do to break in.
Reconnaissance
Five of the IPs appeared to just be performing reconnaissance, as they were simply requesting our home page or some other page on the site. They were likely just checking to see if the site was up and responding to their requests. Since all of the IPs were on the Wordfence real-time IP blacklist, their requests were blocked and they moved on after a couple of blocked page requests.
Author Enumeration
A Chinese IP attempted to retrieve a list of author usernames for the site. Since the authors of posts are very often also administrators, this information can significantly improve the odds of success for a brute force password guessing attack. The attacks all look like the following:
https://www.defiant.com/?author=1
The attacker worked through fifteen author numbers before giving up and moving on. In the Wordfence “Brute Force Protection” settings, look for the following option to enable this feature:
“Prevent discovery of usernames through ‘/?author=N’ scans, the oEmbed API, and the WordPress REST API”
Once you enable this, Wordfence will block these scans. This option is enabled by default and is available for both free and premium users.
Conclusion
As you know, WordPress sites are under constant attack. There are many attackers, all of whom deploy different tactics. The free version of Wordfence includes protection for all of the attacks outlined above. For even better peace of mind, and likely lower attack volumes, consider upgrading to Wordfence Premium. For only $8.25 per month (billed annually) you can put the Wordfence real-time IP blacklist to work protecting your site around the clock.
Jan 2019
![]() As the most popular CMS on the market, one of the major draws of WordPress is a rich ecosystem of plugins made available by the community. The WordPress.org plugin repository makes the process of installing and updating plugins a seamless experience in the dashboard of a site, and a team of volunteers works to maintain the repository as new plugins are submitted and abandoned ones fade away.
As the most popular CMS on the market, one of the major draws of WordPress is a rich ecosystem of plugins made available by the community. The WordPress.org plugin repository makes the process of installing and updating plugins a seamless experience in the dashboard of a site, and a team of volunteers works to maintain the repository as new plugins are submitted and abandoned ones fade away.
The official repository is just one of many places where a site owner can find plugins, though. Since any plugin made available in the WordPress.org repository must be free, third-party marketplaces are a common source of commercial plugins and themes that don’t need to follow the same rules. Some plugin developers even choose to sell their software from their own sites, without involving a marketplace in the transaction.
These third-party sources can be an excellent way to find well-supported commercial plugins for a new WordPress site, offering features that may not be common among free alternatives. However, these sources lack some advantages inherent to the official WordPress.org repository that can cause issues for unaware site owners over time.
In the following post, we’ll be taking a look at two recent examples of security issues in plugins sourced from outside the official plugin repository that are currently being exploited. We’ll also go over some best practices for using commercial plugins responsibly in order to keep your sites secure in the long term.
When a plugin is available on the official repository, WordPress is able to keep track of the version present on your site and compare that to the latest available version. When an update is available, users receive notifications in their dashboard and can issue the update directly from there. In extreme cases of critical vulnerabilities, the repo’s maintainers can even flag vulnerable plugins to automatically update.
Commercial plugins generally lack these protections, as it would rely on the developer to maintain their own repository for all installed copies of their plugins to test against. Updating a commercial plugin often involves manually uploading a new copy, which less-savvy users can be hesitant to do. This also assumes users are periodically checking in on the development process of each of their installed plugins to even become aware that an update is necessary. Since many sites are built by a developer and handed off to the owner to maintain, these owners may not have any idea these extra steps are necessary at all.
In the case of this UserPro vulnerability, we’ve developed a firewall rule to prevent attackers from defining their own role when registering an account.
Third-party marketplaces, as well as developers who self-publish commercial plugins, can be a great source of software for people to add to their WordPress sites. When using these unofficial sources, though, site owners need to remain mindful. These plugins often won’t alert users when an update is available, so even vulnerabilities patched by the software vendor can remain present on sites for a considerable amount of time. Also, when checking your commercial plugins for updates, remain aware of how long it’s been since the last patch. If a plugin hasn’t seen an update in a year or more, consider finding a better-supported alternative.
The UserPro plugin vulnerability has received a firewall rule to block attacks on sites behind the Wordfence WAF. Wordfence users with Premium licenses will have received this new rule by the time this post is published. Free users will gain access to the rule after a standard thirty-day delay.
Oct 2018
WordCamp Atlanta Security Panel with Wordfence – In April, Wordfence sponsored WordCamp Atlanta and several of our team members attended the event. While there, we held a capture the flag (CTF) contest, which helps WordPress site owners learn to think like a hacker so that they can better defend their websites….read more
Three WordPress Security Mistakes You Didn’t Realize You Made – Considering the amount of malicious activity that takes place on the internet, it’s no surprise that successful attacks on WordPress sites are launched across a wide variety of vectors. Whether outdated plugin code is to blame, or password reuse, or any number of other security flaws, no site owner sets out to introduce a vulnerability into their environment. Ultimately any security issue begins with a mistake, and while mistakes are forgivable there’s still risk involved if they’re not discovered and remedied….read more
July 2018
Arbitrary File Deletion Flaw Present in WordPress Core –
The security community has been abuzz this week following the disclosure of a vulnerability present in all current versions of WordPress. The flaw, published in a detailed report by RIPS Technologies, allows any logged-in user with an Author role or higher to delete files on the server.
By exploiting this arbitrary file deletion vulnerability, malicious actors can pivot and take control of affected sites. The report contains the complete details of the vulnerability, but we’ve summarized it for more casual consumption.
In a standard WordPress installation any logged-in user with a role of Author or higher has the ability to upload media attachments and edit their metadata, like images and their descriptions. A flaw in the process of updating attachment metadata allows a malicious user to submit unsanitized input in defining a thumbnail for the media file. By defining relative paths to targeted files as the “thumbnail” of an image, these files would be deleted alongside the actual thumbnails when the image is deleted from the media library.
51 Tools for Security Analysts
Google dorks – Using advanced operators in the Google search engine to locate specific strings of text within search results.
Maltego – An interactive data mining tool that renders directed graphs for link analysis
FOCA – A tool used to find metadata and hidden information in the documents its scans.
https://haveibeenpwned.com/ – Check if an account has been compromised in a data breach.
https://www.beenverified.com/ – Search people & public records.
BuiltWith – Find out what websites are built with.
http://themecheck.org/ – A quick service that lets you verify WordPress themes for security and code quality. OTHERS
March 2018
 The Atlanta Ransomware Situation –
The Atlanta Ransomware Situation –
In mid-March, the City of Atlanta was hit with a ransomware attack. Several major computer systems that provide city services have been encrypted by an attacker. The attacker demanded $51,000 worth of bitcoin to decrypt the systems, and the city was considering paying the ransom.
The City of Atlanta is working with the Secret Service, FBI, Department of Homeland Security and academic and private institutions, including Georgia Tech and SecureWorks. They have completed the investigation and containment phase of the incident response and have moved on to the restoration phase where they work to bring critical systems back online, but at this time the affected systems are still encrypted.
I think this is a valuable lesson, and something that WordPress site owners should take to heart. It is important to be proactive when it comes to securing your systems and educating yourself about cybersecurity. Don’t wait until you get hacked before you take action.
Dec 2017
Breaking: Aggressive WordPress Brute Force Attack Campaign Started Today (12/19)
A massive distributed brute force attack campaign targeting WordPress sites started this morning at 3am Universal Time, 7pm Pacific Time. The attack is broad in that it uses a large number of attacking IPs, and is also deep in that each IP is generating a huge number of attacks. This is the most aggressive campaign we have seen to date, peaking at over 14 million attacks per hour….read more
The attack campaign was so severe that WordFence had to scale up their logging infrastructure to cope with the volume when it kicked off, which makes it clear that this is the highest volume attack that they have seen in Wordfence history, since 2012.
Wordfence was able to isolate the IP addresses from the botnet and then compare them to the IPs from our most recent site cleaning orders. As luck would have it, we got a couple of hits. This afforded us the amazing opportunity to dig in and find out what the attacker is up to, and what we found is really interesting. – Thank goodness for Wordfence!
——————-
While no system is 100 percent hack-proof, there are certain measures you can take to prevent a hacked WordPress site. To
reduce your chances of being affected by a disastrous brute-force or DDoS attack, read below for the most important WordPress
security tasks you should implement to become more proactive against potential threats:
- Keeping Software Up To Date – The most common culprit of a hacked WordPress website is due to an outdated component. Outdated plugins, themes, and core open the portal for a potentially hacked site.
- Avoid Installing Untrusted WordPress Plugins and Themes – To detect if a theme or plugin can be trusted or not, first, read its ratings. There you can find clues to whether there have been security breaches or issues in the past, like buggy updates.
- Don’t Forget To Remove Unused Plugins And Themes – As you start to accumulate themes and plugins, you should go
through and dispose of the ones you no longer use - Install A WordPress Security Plugin – Installing a WordPress security plugin is a no-brainer when it comes to enhancing the security of your site. Become more proactive against security threats.
- Regularly Backup Your WordPress Site –
- Enforce Strong Passwords and Usernames – We’re all guilty of using a password that’s simple to remember. But
using an easy password, say one that contains your birth year, makes
it easier for hackers to crack the code using brute force automated
scripts, which continuously try to guess your password and
username over and over - Use Two-Factor Authentication (2FA) – Enabling 2FA adds an extra layer of security to your login credentials. 2FA works by requiring a second factor of information that only you can give, like a code sent to your phone to verify your activity on a specific computer.
- Change Or Omit The “Admin” Username
- Limit Login Attempts – WordPress doesn’t have a limit as to how many times one can guess a password to login. This presents a problem because determined hackers won’t give up.
- Monitor Incoming Attacks – It’s vital to log incoming security attacks so you’re aware of what’s going on inside your WP installation from a historical perspective.
- Use SSL – Enabling SSL is the next crucial step to a more secure site. SSL (Secure Sockets Layer) encrypts all information sent to and from your site. That way the private data visitors share with your site stays private.
- Hide Your WordPress Version – If you defer WordPress updates, you should consider hiding your WordPress version because it leaves footprints, telling the hacker useful information about your site.
- Relocate Or Rename The Login Page – To make your site more bulletproof, relocating your login page is worth the effort. Not only does it hide the fact that you’re on WordPress, but it limits brute-force attacks on your login page.
- Secure The WP-Config File – The wp-config file contains your website’s base configuration details, like database connection information.
- Use A Secure Hosting Environment – You can follow all of the security measures above, however, if you don’t invest in a secure hosting provider, these efforts are all for nothing.
Nov 2017
Vulnerable themes attacked in Oct were – mTheme-Unus, Canvas, Typebased, TwenyFifteen, Sealight, Sketch, etc.
The most common plugins attached were – wp-mobile-detector, wp-symposium, wptf-image-gallery, recent-backups, candidate-application-form, wp-ecommerce-shop-styling, wp-rocket, etc.
The countries with the most hackers / IP blocks were – Russia![]() , US
, US![]() , China
, China![]() , Ukraine
, Ukraine![]() , Turkey
, Turkey![]() , France
, France![]() , Korea
, Korea![]() , India, Brasil, Netherlands.
, India, Brasil, Netherlands.
Oct 2017
The total attacks from the top 25 attacking IPs decreased by 8% from August. Brute force attacks made up 91% of total attacks for September, the same as August. Complex attacks accounted for 9% of the volume.
![]() Turkey topped the list this month with 11 of the top 25 IPs after having disappeared from the list last month. The four most active IPs were from Ukraine
Turkey topped the list this month with 11 of the top 25 IPs after having disappeared from the list last month. The four most active IPs were from Ukraine![]() , with PP SKS-Lugan hosting three of them.
, with PP SKS-Lugan hosting three of them.
‘REDACTED‘ and ‘Revelance‘ themes were attacked a great deal in the past month w/ ‘mTheme-Unus‘ and ‘RightNow‘ themes being attacked the most!
Sept 2017
The average number of daily brute force attacks was down 9% from last month after growing the previous two months. Daily attack volumes were stable for most of the month, but plummeted on the 27th, dropping by roughly half for the final five days.
Ukraine![]() , Korea
, Korea![]() , followed by the United States
, followed by the United States![]() were the top attacking IP addresses the past 2 months.
were the top attacking IP addresses the past 2 months.
Theme Attacks – The most attacked theme was the ‘twentyseventeen’ theme, followed by the ‘sketch’ theme. ‘0 mTheme-Unus’, ‘Canvas’, ‘Flat-Bootstrap’, ‘Parallelus-Salutation’ were also themes that were heavily attacked.
July 2017
The total attacks from the top 25 attacking IPs decreased slightly from 133 million in June to 124 million in July. Brute force attacks made up an amazing 87% of total attacks for July, up from 67% in June. Complex attacks accounted for 13% of the volume. As usual, the list is dominated by Russia![]() , Ukraine
, Ukraine![]() , Turkey and India followed by the United States
, Turkey and India followed by the United States![]() .
.
This list shows the themes with the greatest total number of attacks. mTheme-Unus, Canvas, Clockstone, Parallelus- Churchope, Dejavu, Elegance, Infocus, Epic, Trinity & Sealight.
This list shows the plugins with the greatest total number of attacks. Wp-Mobile-Detector, WP-Symposium, Recent-Backups, WP-Rocket & Really Simple Guest Post.
June 2017
Backups Are Critical to Your WordPress Security Strategy – If your site is compromised, having access to backups can make your life considerably easier. The fastest way to recover from a hacked website is to restore the latest version of the site that existed prior to the hack. You will still need to close the security hole the attacker used to compromise your site after your site is back up and running, but at least you’ll have your site back to working order in hours or even minutes.
Without a good backup on hand, you’ll need to either manually clean your hacked websiteor pay an expert to do it for you. Many companies provide site cleaning services, including Wordfence. Many of them are quite reasonably priced, but with the right backup service you should be able to avoid this expense altogether.
UpdraftPlus Premium – BackUp Buddy –
May 2017
Top Countries w/ Hackers
Russia 31.184.194.90 – Petersburg Internet Network ltd. ![]()
Ukraine 91.200.12.49 Pp Sks-lugan ![]()
UK 148.253.188.34 Aspire Technology Solutions Ltd ![]()
US 192.187.98.42 DataShack, LC ![]()
Korea 160.202.162.19 Korea Telecom ![]()
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for the IP, so this is not reliable data, but we still include it for interest. For example, we have seen PTR records that claim an IP is a Tor exit node, when, based on traffic, it is clearly not. We also include the city and country, if available.
The total attacks from the top 25 attacking IPs increased from 137 million in April to 144 million in May. Brute force attacks made up 72% of total attacks for May, up from 68% in April. Complex attacks accounted for 28%. Turkey and Ukraine continued to dominate the top 25 list, accounting for 16 of the IPs on the list.
——————————————–
Popular WordPress Security Myths – Because of its incredible popularity as a platform, WordPress enjoys a sizable, generous community of users that spend their time sharing information, resources, tips and insights with other WordPress users online. Understandably, online security is at the forefront of concerns for many site owners, and a lot of the online conversation about WordPress centers around the best ways to keep your site safe from hackers and security breaches.
All That’s Needed to Lock Down a Site Is a Secure Username and Password – Certainly, using a strong password and unique admin username on your WordPress website is an important part of securing your site. After all, one of the basic tactics of hacker bots is to try a few thousand passwords with the default WordPress username “admin.” But the truth is that even if you have a secure username and password for your website, hackers may still be able to break into and take down your website using other means, such as security vulnerabilities in outdated plugins, data breaches or phishing. Sites that aren’t protected by two-factor authentication, which sends a code to your cell phone every time you log in as an admin, are especially at risk of exposure.
My Site Is Safe Because It Has an SSL Certificate – An SSL (or Secure Socket Layer) certificate adds a layer of security to the communication that takes place between your website and your visitors. Unfortunately, the security that an SSL certificate offers your website is purely transactional: it protects the information being passed between your site and your visitors, but – crucially – not the data housed on the site itself.
WordPress Itself Is an Insecure Platform – WordPress is the most popular content management software right now, Due to its popularity, WordPress has endured a few high-profile security scares in the past few years. While it may be the case that WordPress may be subject to more attacks than less popular CMSs, this doesn’t mean that WordPress is inherently less secure. On the contrary, because it powers millions of websites, WordPress has a passionately active international community of users and developers that collectively work 24/7/365 to find and patch any possible security vulnerabilities. The overwhelming vast majority of security compromises and hacking incidents – nearly 80% – are the result of outdated software and/or password exploits – that is, they’re due to either a weak username/password combo, or due to a vulnerability that the site admins failed to patch or fix in time, not an inherent flaw in the software itself.
Maintaining and optimizing the security of your website can seem like a very daunting and complicated undertaking. Site owners may struggle to parse an endless stream of information and advice that sometimes may even conflict. Determining what will really work and what is simply “security theater” can be extremely challenging, but armed with a good endpoint firewall, a secure username and password with two-factor authentication, and the most up-to-date site software, you can get a lot of peace of mind knowing that you’re making it as hard as possible for anyone to get through your website’s well-maintained defenses.
– https://www.wordfence.com/blog/2017/05/7-popular-wordpress-security-myths/
April 2017
The distribution of brute force attacks compared to complex attacks among the top 25 attackers remained roughly the same. 32% of attacks on WordPress sites in April were complex attacks. 68% were brute force attacks. Brute force attacks remain by far the most popular attack method on WordPress sites.
Turkey made up a total of 11 of our top 25 attacking IPs in April. There are a total of 5 separate ISPs in Turkey that contributed to the top 25 attacking IPs.
Attacks on Themes in April 2017 – The most commonly attacked themes on WordPress for the month of April is surprisingly stable. Almost all themes in our top 25 were also in the list last month with a slight reshuffling.
mTheme-Unis, infocus, echelon, elegance, awake, dejavu, churchope, fusion, contruct, epic, authentic, NativeChurch, antioch, trinity, method, persuasion, myriad, modular, parallelus-mingle, infocus2, lote27 & urbancity.
Attacks by Country for April – Our usual suspects are still at the top of the list of the top countries from where attacks on WordPress originate.
Russia, Ukraine, US, Turkey, India, China, France, Brazil, Korea, Phiippines and Italy.
March 2017
What does “Secure” actually mean in Chrome browser?
In order for a website to be labeled as ‘Secure’ by Chrome, it needs to set up SSL on its web server. As part of that process, it needs to contact a certificate authority (CA) to get a ‘certificate’. The CA is supposed to verify that the website owner actually owns the website. This process is called ‘domain validation’. Other than verifying that the domain owner actually owns the website, the CA is not required to do anything else.
In Chrome, when you see “Secure” in your browser location bar, it means that the connection between your browser and the website you are connected to is encrypted. It also means that the person who installed the certificate on the website actually owns the site domain. It does not mean that the domain is “Trusted”, “Safe”, “Not malicious” or anything else.
LetsEncrypt is providing valid SSL certificates to phishing sites
Until relatively recently, CAs would generally not issue an SSL certificate to a site that is obviously trying to pretend it is apple.com or microsoft.com. However, there is a new CA called LetsEncrypt which issues free certificates to websites who want to use SSL.
Even if a CA revokes a certificate, Chrome still shows it as “Valid” and “Secure”.
It turns out that this certificate has been “revoked”. What that means is that Comodo, the CA in this case, realized that the certificate belongs to a malicious website after they issued it and they decided to mark it as invalid.
Because Chrome does not check certificate revocation lists in real-time, it shows the certificate as valid in the location bar and the site as “Secure”. Chrome is unaware that Comodo has revoked the certificate after Comodo realized they should not have issued it in the first place.
What should you do to ensure you stay safe on the web?
The best way to protect yourself against malicious sites, in this case, is to check your web browser’s location bar and read the full website hostname that appears there.
Look at the location bar above. You should see ‘https://www.wordfence.com/….’. When visiting any website that you plan to exchange sensitive data with, check the full hostname after ‘https://’ and before the next forward slash. If you don’t recognize it or if it looks like it has some weird stuff on the end, close the window immediately and think carefully about how you ended up on that website.
Feb 2017
Brute Force Attacks on WordPress in February 2017
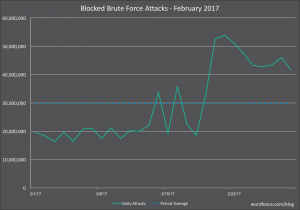
As you can see we experienced a huge spike in brute force attack activity this February starting at approximately February 20th and sustaining until the end of the month. As a reminder, these are simply login guessing attacks. Wordfence blocked an average of 30 million brute force attacks per day across the websites that we protect in February. This is an increase from the 26 million attacks per day average we saw in January.
Attacks on Themes for February 2017
Once again we are not seeing much change in the rankings in the themes that are targeted for attack in WordPress. mTheme-Unus | ChurchOpe | Lote27 | Authemtic | Echelon | Elegance | Awake | inFocus | Dejavu | Persuasion | Fusion | Construct are the MOST attacked.
Attacks on Plugins for February 2017
Our biggest gainer among attacked plugins in February is wp-pagenavi which gained 28 places. Attackers occasionally install fake versions of this plugin once a site is compromised. These may be attempts by attackers to access a fake plugin as part of a check to see if a site has been compromised. These are blocked by Wordfence. – WP-Symposium, WP-ecomerce-shop-styling, recent-backups, candidate-application-form, wptf-image-gallery, wp-mobile-detector are the MOST attacked plugins.
Attacks by Country for February 2017
Russia, US, France, Ukraine, Turkey, Netherlands, India, Chine, Germany, Italy are where most attacks are initiated.
That concludes the attack report for February 2017. I hope this has given you a clear picture of the threat landscape that confronts WordPress currently. In this report the new topology analysis we included has provided unique insight on how threat actors spread themselves across countries and hosting providers.
We saw a huge spike in brute force attacks in February and an average drop in the number of complex attacks. There was little change in the attacked themes and some change in the plugins we are seeing targeted.
Jan 2017
(From Airtable) Most Active IPs
In the table below we have listed the most active attack IPs for December 2016.
193.201.224.205 31.8 – Ukraine ![]()
185.159.36.6 12.4 – Russia Phoenix ![]()
91.200.12.92 6.3 – Ukraine![]()
91.220.131.134 6.0 – Russia Petersburg![]()
178.137.83.84 5.6 – Ukraine Kyivstar![]()
195.154.252.171 5.5 – France ![]()
Complex Attacks vs Brute Force Attacks
A brute force attack is a password guessing attack that is simplistic and has a low likelihood of success. At Wordfence we consider a ‘complex’ attack to be an attack that tries to exploit a vulnerability in WordPress or a WordPress plugin. If you are using Wordfence to protect your WordPress website, brute force attacks are blocked by our brute-force protection and complex attacks are blocked by the Wordfence firewall. The top two IPs, one in Ukraine and one in Russia, are both using complex attacks to target WordPress websites.
Brute Force Attacks
If you recall our post on December 16th where we described a “Huge Increase in brute force attacks in December“, we saw a marked increase in the number of attacked sites starting in late November.
https://managewp.com/2016-wordpress-website-maintenance-survey
http://torquemag.io/2016/03/wordpress-sites-hacked/
https://www.onehoursitefix.com/10-ways-to-prevent-your-wordpress-website-from-being-hacked/
https://www.cloudways.com/blog/wordpress-hacked-8-tips-to-harden-wordpress-security/
https://www.wordfence.com/docs/how-to-clean-a-hacked-wordpress-site-using-wordfence/

